In this day i have try some new cool technology that i love…
Honeypot
What they are? a honeypot is a fictional vulnerable system used to attract malicius software in the intent of use the fake bugs on the server and at the same time to grab information about the attacker and the technics used for attacks. A honeynet is a network of two or more honeypot.
All the data retrived by a honeypot can be used for many reason, try to make a profile of the attacker, for research tring to steal the exploit and 0day stuff used by the attacker and know new vulnerability and can also be used in a legal procedure.
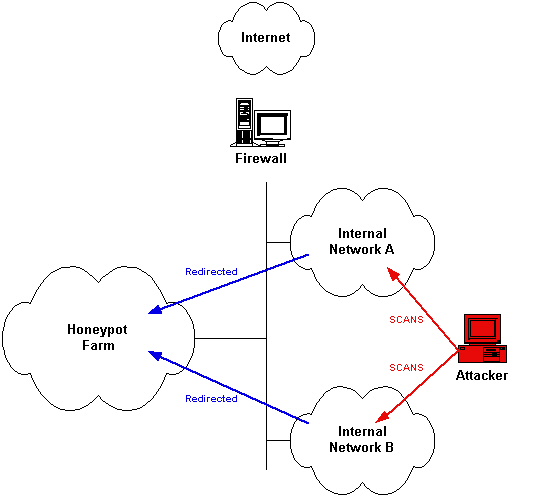
The honeypot are divided in three level depending on how deep an attacker can interact with it
Low interation are emulated by software and the interaction is really inconsistent
medium interaction they are chrooted or jailed and provide a limited system access
high interation the attacker can have full access on the server
they are also classified on the data that they can collect
Production can collect only limited information
Research can collect more information about the attacker and the strumentation used for the attack, they are used for reasearch by goverment and military.
Another version of honeypot are used for capture spammers giving fake smtp convicing the abuser that is a usable smtp relay for sending all sort of email when in fact is not and also can try to intercept the ip of the illegit user.
Some honeypot can also try to assorb and reverse the malware when it try to attack the fake server for research analysing the binary file.
Some honeypot software can be:
Labrea is a tarpitting honeypot used for deceive the attacker scanner showing faking server with all port open in the unused network ip web adress for tarpitting but this can be useless with multithreading scanners.
Nepenthes is a good botnet detector and tracker and can also try to reverse the binary file and shellcode

Dionaea the successor of nepenthes developed by the same team http://dionaea.carnivore.it/ and is a part of the google summer code.
Honeyd is a small daemon need for create virtual hosts on a network. this virtual host created can be configured for attract intruder of specific vulnerability.
For make a honeypot work you have to be really patient !!! and wait…
a intruder can take lot of time before try to compromise it.
The best is to have a firewall and other security tools for have the most possible data and information about the intrusion.
